Venko works in the security front with two different approaches: providing traditional Firewall solutions or through a disruptive perspective, in a concept using Zero Trust and Software Defined Parameter. This later approach is very innovative, and has been adopted in highly sensitive industries such as financial markets, governments, energy plants, among others).

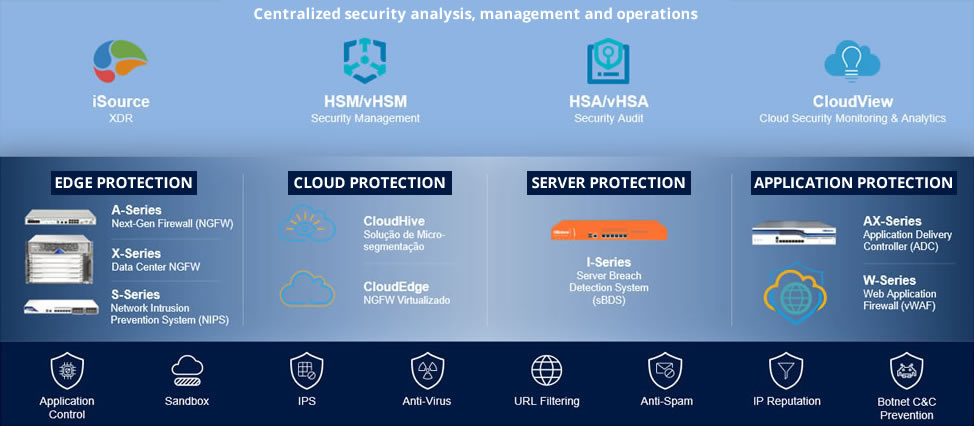

Extended Detection and Response (XDR) Solution
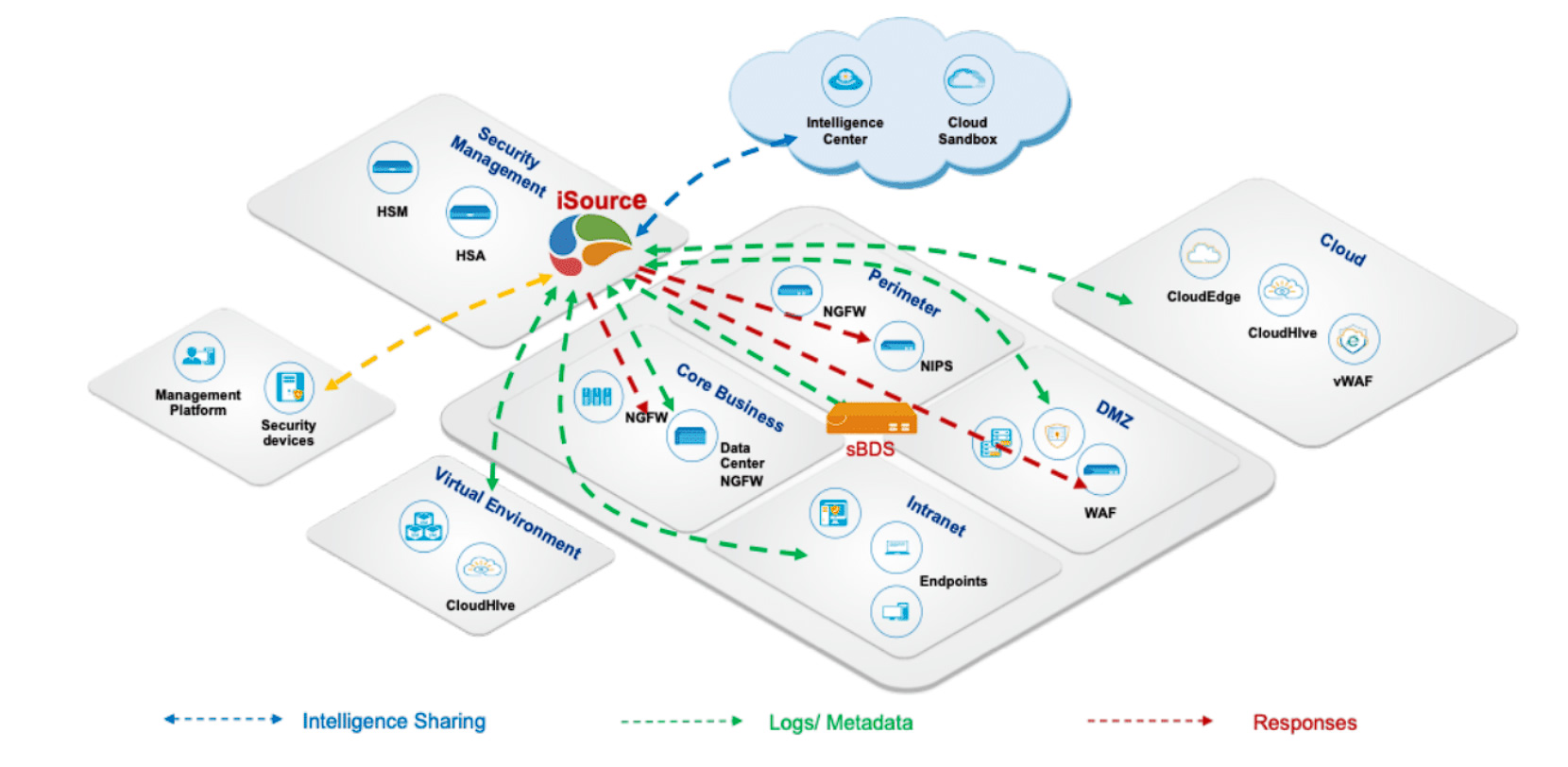
Hillstone iSource is a data-driven, AI-powered extended detection and response (XDR) platform that integrates massive security data, investigates correlations of incidents, identifies potential threats, automates security orchestration and responds cohesively across multiple security products and platforms. It brings a radical new approach to cybersecurity with complete visibility, highly accurate threats identification and swift containment and mitigation for unrivaled security operation efficiency.
Hillstone iSource collects various types of data, such as threat logs and incident reports, from almost any source across Hillstone’s product stack and as well as 3rd party products. By standardizing and integrating heterogeneous data across components, including cloud, network and endpoints, iSource breaks down security information silos. It not only brings full security visibility with far fewer blind spots, but also improves detection accuracy and provides effective and efficient defense against threats.
Hillstone vulnerability management helps identify and present vulnerabilities by leveraging the industry’s leading vulnerability assessment solution. It also supports adding new scanners for customization or even manually importing a vulnerability report file for further containment of threats. Assets are the core for risk management. Hillstone iSource provides comprehensive risk management to assets like servers, endpoints, or even applications and services, from multiple dimensions including risks, vulnerabilities and threat events. It presents statistical data, such as distribution and trends of threats and vulnerabilities, along with detailed information of individual assets. This holistic approach protects assets by identifying and mitigating potential exposures to threats
By synergizing the data and logs collected across the entire security fabric, as well as threat intelligence from top threat intelligence sources, Hillstone iSource can discover even stealthy and evasive threats, and attribute the attacks. Powered by machine learning technology and statistical algorithms, its behavior analytics engine helps distinguish anomalous activities among a large amount of integrated data. Its correlation analysis engine consolidates individual incidents for context awareness, and applies analysis to correlated data to identify high-fidelity incidents, provide a complete picture of an attack chain and further help in the investigation of the attack’s purpose. Its powerful log analysis has built in threshold- and status-based detection and correlation analysis capability that allows security analysts to define customizable rules to identify key threats via artifacts. The Search Processing Language (SPL)-based log search engine also alleviates the pain of searching and analyzing massive logs.
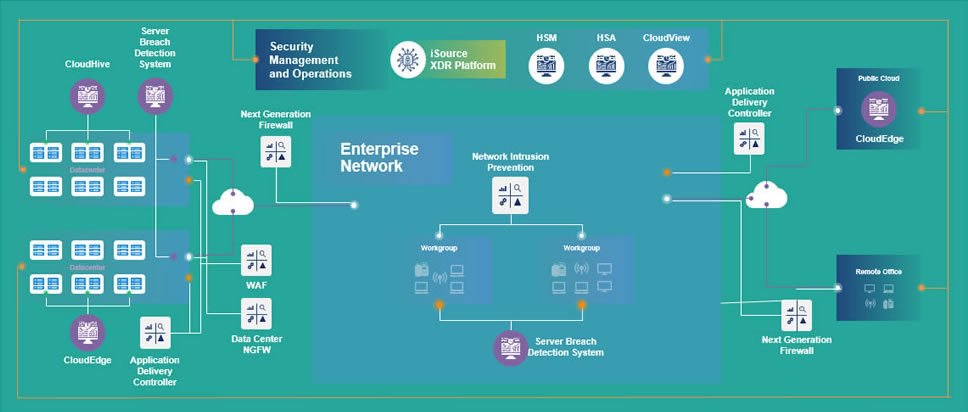
Hillstone iSource offers automated security orchestration and response capability with built-in playbooks, integrated interactions with Hillstone security products and the ability to assign tasks for collaborative case management. Besides predefined playbooks that offer optimized workflows and responses, Hillstone iSource also offers the agility and flexibility to define automated workflows visually in playbooks based upon ingested incidents or alerts, intelligence queries and actions of response. These playbook-driven responses combine automated tasks that can span multiple Hillstone devices, such as Hillstone NGFW, NIPS, CloudEdge, CloudHive, etc., with manual tasks handled respectively through incident case management. Certain 3rd-party devices can also be supported in playbooks via RESTful APIs or SSH connection. This enables swift incident triage and attack containment before damage can be done.
The customizable dashboard allows simple and rapid access to the organization’s security posture with comprehensive statistical information such as rankings and counters, as well as incident summarization and security trends with graphical charts and lists. The intuitive design provides an optimized user experience for management and operations. Hillstone iSource also supports template-based or customizable reports that can be generated on schedule or on demand. Public APIs enable integration with third-party tools or security products to inject security data generated across the entire security fabric and perform interactions to contain threats.
Server Breach Detection System (sBDS)

The Hillstone Network detection and response (NDR) product Server Breach Detection System (sBDS) adopts multiple threat detection technologies that include traditional signature-based or rule-based technology and large-scale threat intelligence data modeling, as well as machine learning-based user behavior analysis. The system provides an ideal solution for detecting advanced threats, including ransomware and crypto-mining malware, and protecting high-value critical servers and sensitive data from being leaked or stolen. Together with deep threat hunting analytical capabilities and visibility, Hillstone sBDS provides security admins the effective means to detect IOCs (Indicators of Compromise) events, locate risky hosts and servers, and restore the attack kill chain. Moreover, it conducts threat and attack mitigation with the conjunction of NGFW, as well as with the integration of Hillstone XDR system iSource. The Hillstone NDR product sBDS brings an effective and comprehensive solution to detect and respond to different breeds of network attacks and threats in an enterprise’s assets.
Cyber attackers have become ever more sophisticated, using targeted, persistent, stealthy and multi-phased attacks, which can easily evade perimeter detection. Hillstone sBDS consists of multiple detection engines focused on different aspects of post-breach threat detection, including advanced malware detection (ATD), abnormal behavior detection (ABD), as well as traditional intrusion detection and virus scanning engines. Hillstone’s threat correlation platform analyzes the details of the relationships of each individual suspicious threat event as well as other contextual information within the network, to connect the dots and provide accurate and effective malware and attack detection with high confidence levels.
The Hillstone sBDS platform focuses on protecting critical servers within the intranet, detecting unknown and near 0-day threat attacks and finding abnormal network and application level activities of server and host machines. Once a threat or an abnormal behavior is detected, Hillstone sBDS will perform threat or behavioral analysis and use topology-based graphic presentations to provide extensive visibility into the threat details and behavioral abnormalities. This gives security admins unprecedented insights into the attack progress, traffic trending in each direction, as well as the entire network risk assessment.
IOCs events are threat events detected during the post breach attack. They are identified among large numbers of the threat attacks in the network that are directly associated with the protected server or host. IOCs are typically seen as threat activities with higher risk and with a high confidence level that a server or host is being compromised and that poses a potentially bigger threat to the critical assets within the corporate network. To effectively detect IOCs and perform deep threat detection on these IOCs is critical in throttling the goal of stealing important data from critical assets, and preventing a threat attack from further spreading within the network. Hillstone sBDS drills down and surfaces more threat analysis and intelligence on these IOC events, reconstructing the attack chain based on these IOCs and correlating other threat events associated with these IOCs within time and space spectrums.
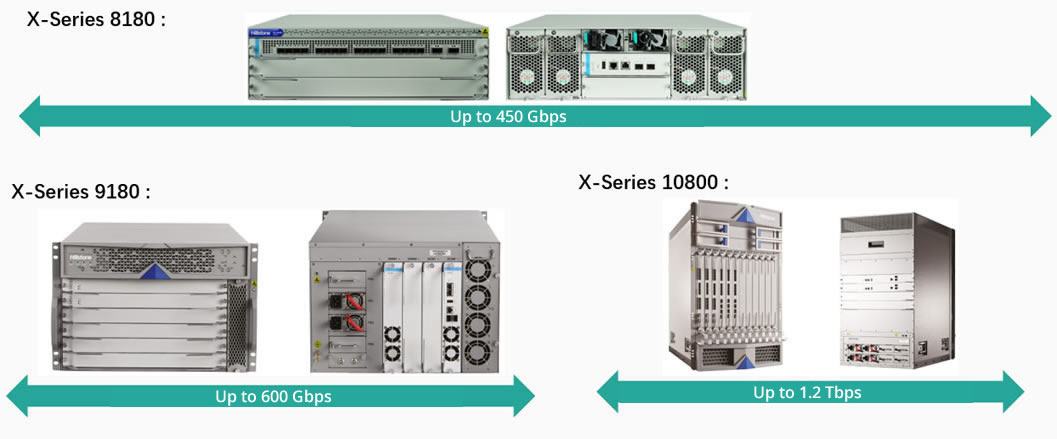
The Hillstone sBDS platform conducts threat mitigation with conjunction of Hillstone A-Series NGFW, E-Series NGFW, and X-Series data center NGFW devices, which are positioned at the network perimeter. After the security admin or network operators analyze and validate threat alerts, they can add threat elements such as IP addresses, type of threats etc., to the blacklist or security policies, and then synchronize them to the Hillstone firewalls so that future attacks from the same breeds or malware family can be blocked at the network perimeter. This prevents future attacks from spreading to broader network territories.
